The EU Regulation DORA (Digital Operational Resilience Act) establishes a unified framework for the European financial sector to manage cybersecurity and ICT risks. Its goal is to strengthen the EU financial market by harmonizing requirements and standards in cybersecurity and ICT risk management, ensuring resilience and adaptability—operational resilience—of financial institutions during and after disruptions. Implementation is required by 2025, but how can this be achieved with manageable effort? This blog post provides an overview of DORA and offers practical tips for implementation.
DORA Applies from Early 2025
The Digital Operational Resilience Act affects nearly all regulated institutions and companies in the European financial sector, including banks, insurance, and reinsurance firms. Companies must act now: the regulation came into force in January 2023 and will apply from January 17, 2025, after a two-year transition period.
In January 2024, the European Supervisory Authorities (ESAs)* published the first final drafts of technical regulatory and implementation standards—a set of standards to ensure consistent regulation of operational processes.
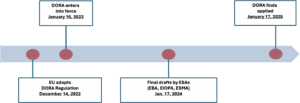
Figure 1 : EU Regulation DORA – Contents and implementation tips
*= The European Supervisory Authorities (ESAs) include:
EBA: European Banking Authority
ESMA: European Securities and Markets Authority
EIOPA: European Insurance and Occupational Pensions Authority
What DORA Regulates
The EU Regulation DORA aims to strengthen resilience against cyberattacks and digital security. It sets requirements for cybersecurity, business continuity, and crisis management to ensure processes remain available during cyberattacks or technical failures. It focuses on ICT risk management and aligns with national and international best practices.
DORA covers six key areas:
| Area | Key Features |
|---|---|
| ICT Risk Management: |
|
| Reporting on ICT incidents and significant cyber threats: |
|
| Testing digital operational resilience and threat-led penetration testing (TLPT): |
|
| ICT third-party risk management: | Contract components, e.g., necessary components such as support from the service provider in the event of incidents |
| European supervisory framework for critical third-party ICT service providers: | Monitoring of critical IT service providers (critical, for example, in terms of the impact of operational disruptions on the entire financial market / number
of customers or many systemically important financial companies as customers) |
| “Information sharing” and cyber crisis and emergency drills: | Information exchange (at EU level) => Derive measures => Continuous improvement |
Incident Reporting Framework
With regard to the implementation of DORA, uniformly regulated reporting processes for incidents in European financial companies are an important aspect. Parallels to the reporting obligation can also be found, for example, in the NIS2 Directive. Incidents are first reported to the competent national authority and assessed with the involvement of the European supervisory authorities. If relevant, they are then forwarded to other member states and other authorities. Figure 2 shows an incident in the DORA reporting process with BaFin as the central element in interaction with BSI and European supervisory authorities:
DORA regulatory and implementation standards
The above-mentioned drafts of technical regulatory and implementation standards (RTS and ITS) published by the ESAs are intended to support and facilitate implementation: The regulatory technical standards (RTS) contain detailed, specific rules and technical requirements, e.g. with regard to ICT risk management and security measures for IT systems, while the implementing technical standards (ITS) contain specific rules or procedures, e.g. instructions for conducting security tests or reporting security incidents.
The European Commission reviews these drafts to ensure that they are in line with European laws and policy objectives. They will become the binding standard for the implementation of DORA. As these standards specify the requirements of DORA in concrete terms, they also enable a better assessment of the implementation costs for companies.
Distinction from other regulatory requirements
DORA overlaps thematically with other current regulations and directives, such as the NIS2 Guidline, which aims to strengthen the overall level of cybersecurity in the EU, and TIBER (Threat Intelligence-based Ethical Red Teaming), which aims to promote resilience against cyberattacks through preventive testing. If a company also falls under the NIS2 Directive, the following applies: If the DORA requirement is more specific, it takes precedence.
For the banking sector, the European Banking Authority (EBA) published the EBA Guidelines on Outsourcing and Guidelines on ICT and Security Risk Management in 2019, defining risk management measures relating to information security and outsourcing requirements. However, these are recommendations or guidelines that only apply to the banking sector.
The DORA Regulation basically includes the content of these requirements and guidelines. DORA focuses on the consistent standardization of known regulations and requirements in the context of operational stability and business continuity. Unlike the EBA guidelines, it affects not only the EU banking sector, but the entire EU financial sector.
How does DORA integrate into German financial regulatory requirements?
There are a number of regulations issued by the German regulatory authority BaFin, such as BAIT (Banking Supervisory Requirements for IT). BaFin is also responsible for implementing DORA at the national level, including monitoring and control. It also has another important role: it is the central reporting office for ICT incidents and the link in cooperation with other national supervisory authorities and the EBA. In doing so, it works together with the European supervisory authorities to ensure consistent enforcement across the EU.
BaFin has also established requirements and practices in the German financial sector in the past that are now reflected in DORA:
- Harmonized requirements for ICT risk management
e.g., minimum requirements for risk management (MaRisk), IT requirements in BAIT, ZAIT, VAIT, KAIT - Standardized reporting of outsourcing
i.e., uniform standards and procedures for reporting outsourcing to BaFin - Monitoring of IT service providers with multiple clients
- Standardized structures for reporting ICT-related incidents
Key elements are reflected in DORA. Therefore, the BaFIn requirements that have already been implemented provide a good basis for the implementation for the DORA regulation in companies.
Recommendations for action and tips for implementation
- Requirements/processes/methods that have already been implemented or established, e.g., from the EBA guidelines, provide a good basis for implementation for financial companies.
- Requirements for documentation and reporting obligations should be reviewed and processes adapted.
- Existing service provider contracts must be reviewed and, if necessary, adjusted, for example, with regard to the support to be provided by the service provider in the event of incidents. (Adjustments can be extremely time-consuming!)
- Existing tools for risk management/documentation/reporting can be used to provide support, e.g., tools for automatic detection and alerting of anomalies, or tools for encryption and management of cryptographic keys, or for implementing lifecycles for firewall rules to strengthen network security.
- New tools for documenting service provider contracts and information registers on service providers required for reporting obligations must be established.
- Findings or measures from the implementation of the Supply Chain Act can also be helpful for the risk assessment of service providers (despite the primary focus on social and environmental standards).
- Overall, specific requirements must be aligned with the (technical and organizational) standards already in place within the company, and processes must be adapted and adjusted accordingly.
Conclusion







